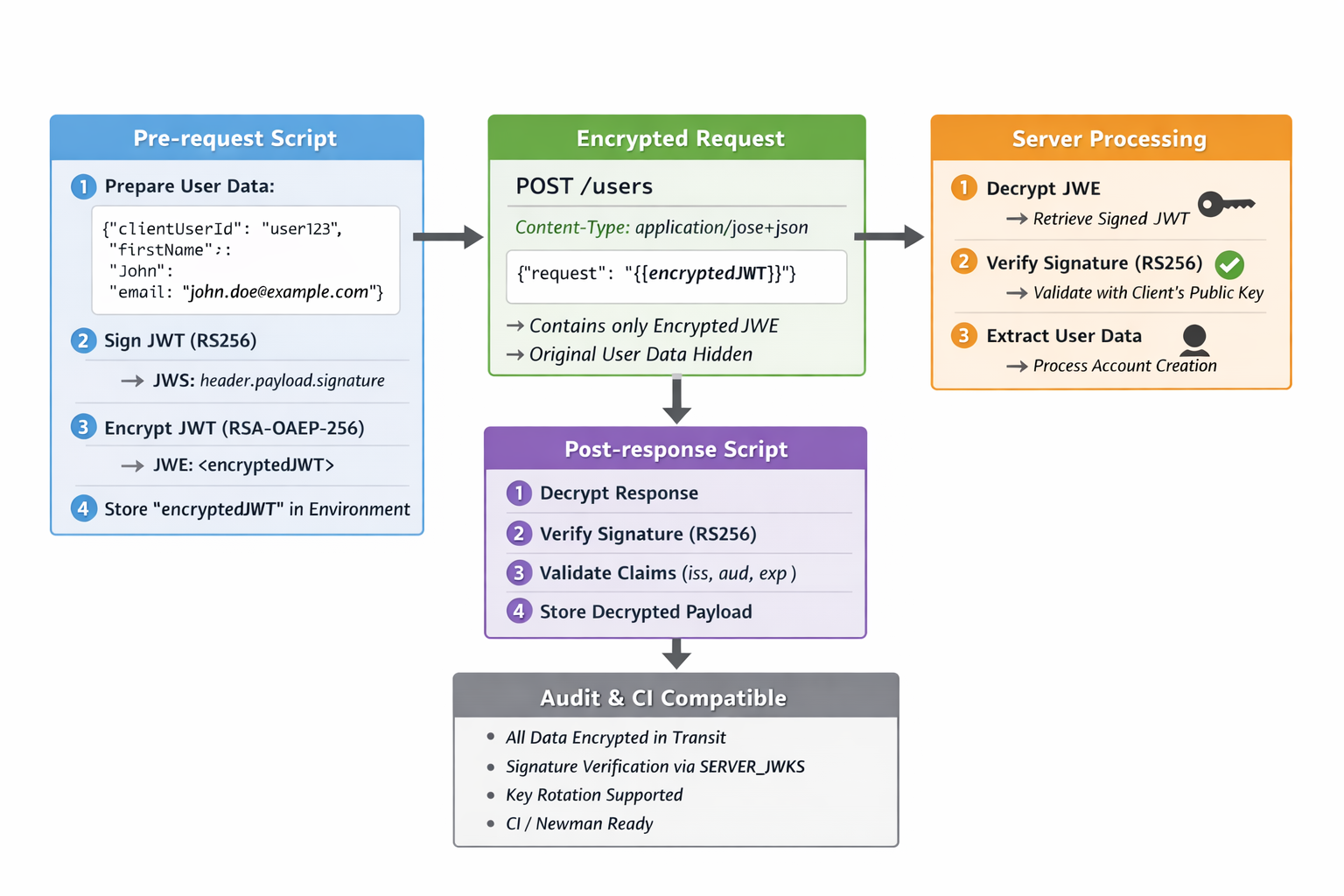
🔑 Post-response Script
// Decrypt + Verify Response
pm.test("Encrypted response present", () => {
pm.expect(pm.response.text()).to.be.a('string').and.not.empty;
});
const privateJWK = JSON.parse(pm.environment.get('PRIVATE_JWK'));
const serverJWKS = JSON.parse(pm.environment.get('SERVER_JWKS'));
const encrypted = pm.response.text();
let decryptedJWS;
pm.test('JWE decrypted successfully', () => {
decryptedJWS = KJUR.crypto.Cipher.decrypt(encrypted, KEYUTIL.getKey(privateJWK), 'RSAOAEP256');
pm.expect(decryptedJWS).to.be.a('string');
});
const header = JSON.parse(KJUR.crypto.Util.b64utoutf8(decryptedJWS.split('.')[0]));
pm.test('JWS header contains kid', () => { pm.expect(header.kid).to.exist; });
const serverKey = serverJWKS.keys.find(k => k.use === 'sig' && k.kid === header.kid);
pm.test('Hyperwallet signing key found', () => { pm.expect(serverKey).to.exist; });
const signatureValid = KJUR.jws.JWS.verify(decryptedJWS, KEYUTIL.getKey(serverKey), ['RS256']);
pm.test('Response signature valid', () => { pm.expect(signatureValid).to.be.true; });
const payload = JSON.parse(KJUR.crypto.Util.b64utoutf8(decryptedJWS.split('.')[1]));
const now = Math.floor(Date.now() / 1000);
pm.test('iss valid', () => { pm.expect(payload.iss).to.eql(pm.environment.get('EXPECTED_ISS')); });
pm.test('aud valid', () => {
const expectedAud = pm.environment.get('EXPECTED_AUD');
if (Array.isArray(payload.aud)) { pm.expect(payload.aud).to.include(expectedAud); }
else { pm.expect(payload.aud).to.eql(expectedAud); }
});
pm.test('token not expired', () => { pm.expect(payload.exp).to.be.above(now); });
pm.environment.set('DECRYPTED_RESPONSE', JSON.stringify(payload));